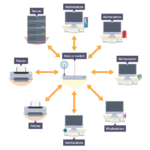
A network is created when more than one device is connected together. A network can be a small collection of computers connected within a building (eg a school, business or home) or it can be a wide collection of computers connected around the world.
Networks can generally be put into two main types:
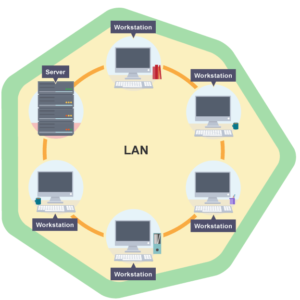
- LAN – Local Area Network
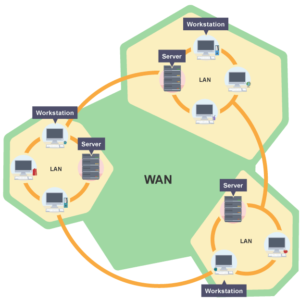
- WAN – Wide Area Network
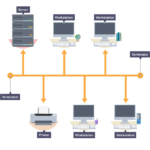
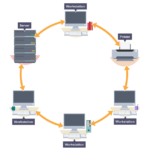
A LAN is a collection of computers, servers, printers and other networked devices connected together in a network. This devices are connected together at the same physical location.
A WAN is a network of devices or other LANs connected over greater distance. The internet is an example of a WAN, or two offices connected together.